Tag: Cybersecurity
-

Enterprise Threat Modeling with AI-Powered Simulations
In today’s digital-first world, enterprises are managing sprawling IT environments that span hybrid clouds, microservices, APIs, and remote workforces, all while trying to stay ahead of an increasingly sophisticated and automated wave of cyber threats. Traditional approaches to threat modelling, typically static, manual, and reactive, are no longer sufficient to protect modern infrastructure. To meet…
-

How Intent-Based Networking Elevates Enterprise Security Posture
Enterprise networks are more dynamic, complex, and critical than ever before. As organisations accelerate their digital transformation, traditional network management models struggle to keep up with the scale, speed, and sophistication of emerging threats. Enter Intent-Based Networking (IBN), a paradigm that aligns network behaviour with business goals while automating enforcement, monitoring, and remediation at scale.…
-

How to Secure APIs in a Multi-Cloud Environment
As modern enterprises move toward digital transformation, adopting multi-cloud environments has accelerated. Organisations now distribute workloads across multiple cloud service providers (CSPs) such as AWS, Azure, and Google Cloud to optimise cost, performance, and reliability. At the heart of this ecosystem are Application Programming Interfaces (APIs), which facilitate communication between services, platforms, and data sources.…
-
The Ethical Tightrope: Navigating the Rise of AI Agents
Artificial Intelligence (AI) agents are no longer confined to science fiction. From chatbots that mimic human conversation to autonomous systems that make financial decisions, AI agents are weaving themselves into the fabric of daily life. Yet, as these systems grow more sophisticated, they bring with them a host of ethical concerns that demand urgent attention.…
-
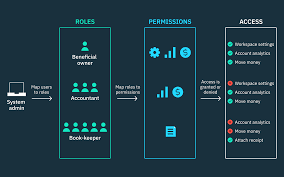
RBAC vs. ABAC: Choosing the Right Access Control Model for Your Business
The Access Control Dilemma In today’s digital landscape, securing sensitive data is non-negotiable. Businesses in Lagos and globally face a critical choice: Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC). Both models protect data but cater to different needs. At JustWebTech, we break down their strengths, weaknesses, and ideal use cases to help you…