The Access Control Dilemma
In today’s digital landscape, securing sensitive data is non-negotiable. Businesses in Lagos and globally face a critical choice: Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC). Both models protect data but cater to different needs. At JustWebTech, we break down their strengths, weaknesses, and ideal use cases to help you decide.
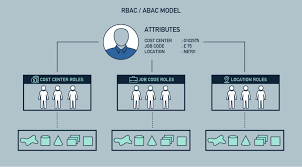
Security Comparison: RBAC vs. ABAC
RBAC: Simplicity Meets Security
RBAC secures data by assigning permissions based on predefined roles, such as “admin,” “manager,” or “guest.” For example, an e-commerce startup might restrict payment gateway access to admins only, while customer service agents can only view order histories. Limiting access to only what’s necessary reduces the risk of accidental or intentional data breaches.
RBAC’s strength lies in its predictability. Roles are static, making it easier to enforce consistent security policies. However, it struggles with dynamic scenarios, like granting access based on a user’s location or time of day.
ABAC: Context-Aware Protection
ABAC takes security a step further by evaluating attributes —user location, device type, or even time of access—to grant permissions dynamically. For instance, a Lagos bank could use ABAC to allow transactions only from trusted IP addresses during business hours, adding layers of protection.
This model excels in complex environments but requires meticulous setup. Each attribute (e.g., “user department = finance”) must be defined, which increases administrative effort.
Manageability Comparison: Ease vs. Flexibility
RBAC: Streamlined for Small Teams
RBAC is easy to implement and maintain, especially for businesses with clear hierarchies. Assigning roles like “developer” or “content editor” simplifies onboarding and reduces errors. For startups juggling limited resources, RBAC offers a practical way to manage permissions without constant oversight.
However, scaling RBAC can become cumbersome. Adding new roles for every scenario may lead to a “role explosion,” complicating audits and updates.
ABAC: Power for Complex Organizations
ABAC’s flexibility shines in enterprises with dynamic needs. Policies adapt to real-time factors, such as granting access only if a user’s device is compliant with security standards. But this complexity demands expertise. Defining and testing attribute combinations requires time and skill, making ABAC better suited for mature organizations.
Combining RBAC and ABAC: The Best of Both Worlds
While RBAC and ABAC are often compared, they can work together. Start with RBAC for foundational role-based permissions, then layer ABAC for context-specific rules. For example, a Lagos healthcare app might use RBAC to restrict patient records to doctors and ABAC to allow access only during emergencies.
When to Choose RBAC or ABAC
RBAC Fits :
Small Businesses: Ideal for startups with straightforward hierarchies
Stable Environments: Works well where access needs don’t change frequently.
ABAC Fits :
Enterprises: Perfect for organizations handling sensitive data (e.g., finance or healthcare) requiring dynamic controls.
Global Compliance: Aligns with GDPR or PIPL by adapting policies to regional laws.
How JustWebTech Can Help
At JustWebTech, we guide businesses to implement the right access control model:
RBAC Solutions: Streamline permissions for SMEs with clear role structures.
ABAC Integration: Build adaptive policies for enterprises with complex needs.
Our programs also equip teams to manage these systems effectively.
Secure Your Systems Strategically
Choosing between RBAC and ABAC depends on your business’s size, complexity, and goals. RBAC offers simplicity and clarity, while ABAC provides granular, context-aware security. By aligning with JustWebTech’s expertise, businesses can implement the model that best safeguards their data and scales with their growth.
Leave a Reply